Sense is Bought Dearly. Forethought is Free.
Why a €0 security protocol is the only thing standing between your business and a €10,000 loss.
We usually picture hacking as a brute-force attack on big corporations. The reality of the current Google Ads takeover surge is far more unsettling. It is targeting businesses like yours. It is quiet. It is polite. It wipes you out because you invited it in.
You are likely doing the work of the CEO, the CMO, and the admin assistant all at once. The phishing email sitting in your inbox is a Mimic designed to exploit exactly that.
Scam in a Fancy Suit
This scam is wearing a tailored suit made of Google’s exact branding. He speaks in the perfect corporate font. He arrives during your busiest hours, mimicking a standard notification so effectively that you don't switch into "security mode." You just switch into "get it done" mode. He doesn't look like a threat; he looks like a to-do list item.
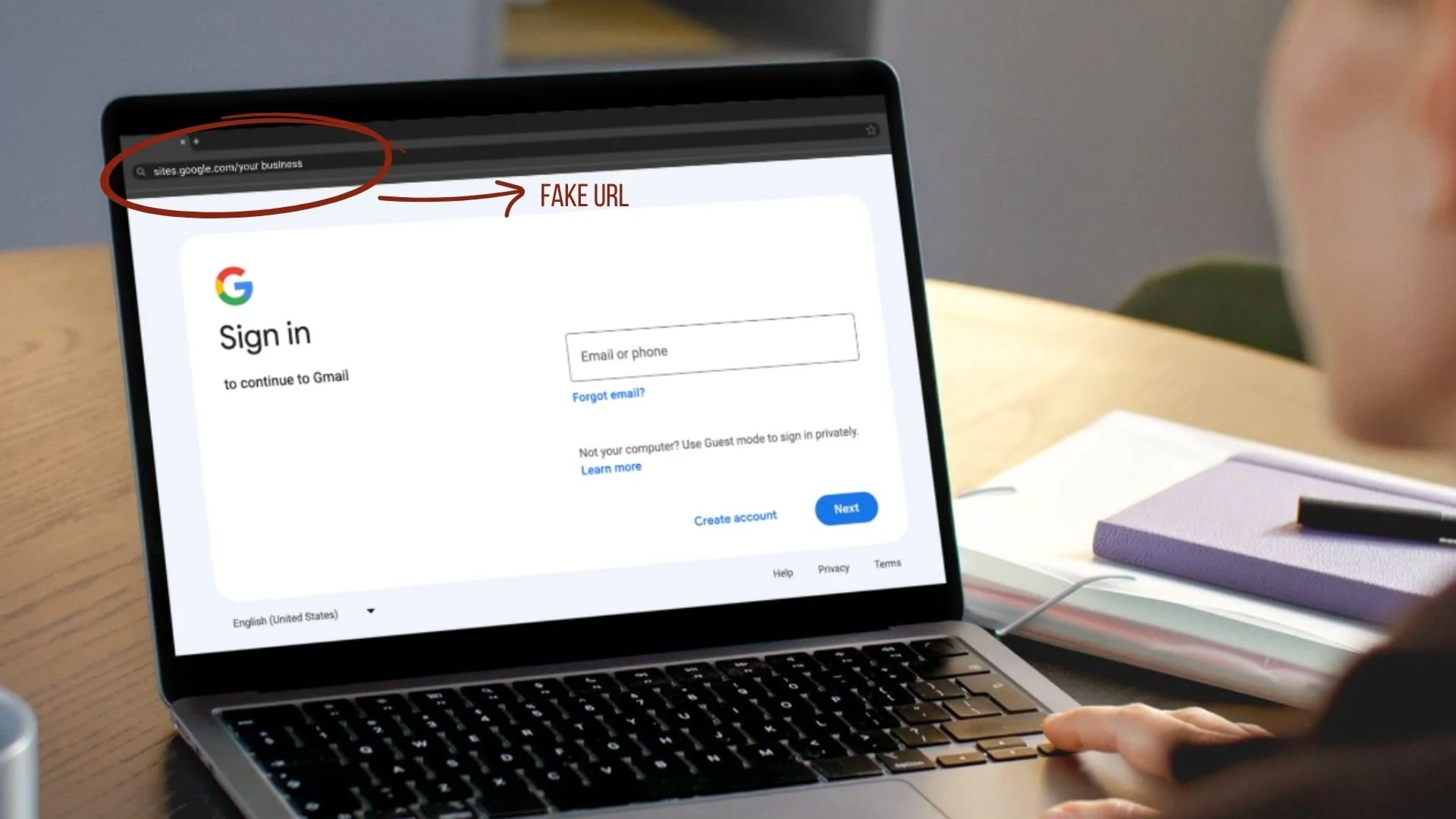
Once you click, you aren't taken to a shady website. You are directed to a Google Sites page. It looks legitimate because, technically, it is hosted on Google’s infrastructure. When you enter your credentials, the Mimic captures them in real-time, bypasses your Two-Factor Authentication (2FA), and hands the keys to an automated bot.
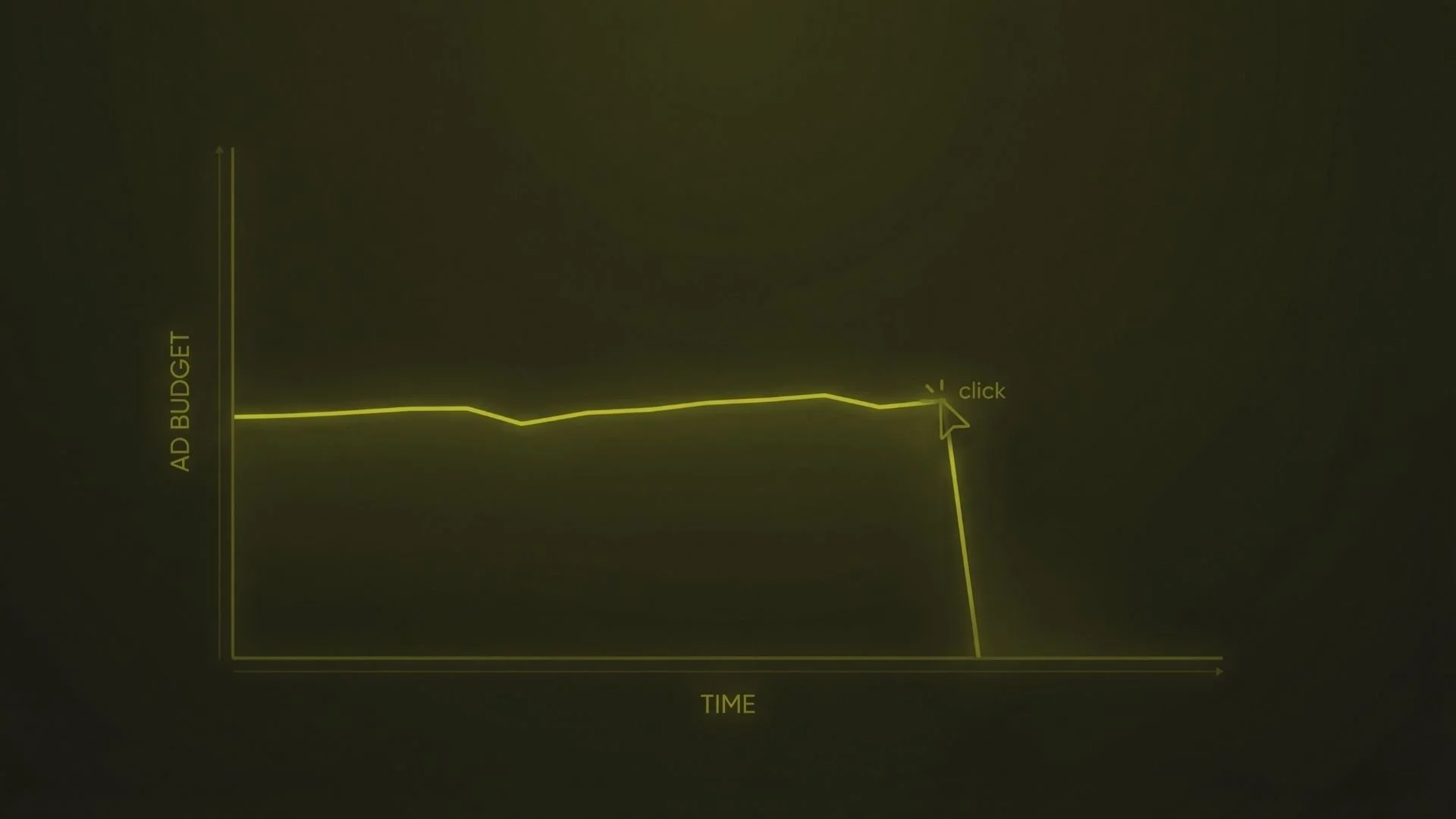
Within hours, the bot locks you out and drains tens of thousands in ad spend on fraudulent campaigns.
Security is Business Infrastructure
We often mistake "infrastructure" for software or strategy. But true infrastructure includes the gates that protect what you have built.
Small business owners often view cybersecurity as "IT's problem." This is a fallacy. In most cases, you probably are IT. If you lose your Ad Account, you aren't just losing a password. You are facing an extinction event for your revenue stream.
Cost of the Click
Cash Flow is drained instantly: Attackers can burn through your monthly budget in 24 hours.
Momentum is killed: While you fight to get access back, your lead generation stops. Your "always-on" engine is dead.
Recovery is slow: Google support can take days to resolve these takeovers. That is days of zero revenue and maximum stress.
My philosophy is simple: Good is not good enough. High standards are the ultimate efficiency. Implementing a rigid security protocol is not paranoia; it is quality control for your livelihood.
The Protocol: Forewarned is Forearmed
You do not need to hire a cybersecurity firm to defeat the Mimic. You just need to stop moving on autopilot.
"Sense is bought dearly" means learning this lesson after the money is gone. "Forethought" is the free alternative.
The URL is the Only Truth The Mimic relies on visual trust—the logo, the colours. Ignore them. Look at the URL. Google never uses
sites.google.comfor login pages. If the login page is hosted on Google Sites, close the tab immediately.The Internal Validation Rule Never accept a notification via email alone. If an email says there is an issue with your ads, open a fresh tab, go to Google Ads yourself, and check the notifications bell. If the alert isn't there, the email is a lie.
Close the Back Doors Have you worked with freelancers or agencies in the past? Are they still users on your account? A cluttered user list is a vulnerability. Remove anyone who doesn't need active access today. If their email gets hacked, your business pays the price.
The Bottom Line
The sophistication of these attacks means that 2FA is no longer a silver bullet. The only defence is a human one.
The Mimic is counting on the fact that you are busy. He is betting that the "Intern" in you will click the link before the "CIO" in you checks the URL.
Protect the business you have built. Don't pay the “auto-mode” tax. Read before you click.